Image Credit: Microsoft
Securing Azure Networks: NSG vs. ASG
When it comes to protecting your workloads in Azure, two tools stand out: Network Security Groups (NSGs) and Application Security Groups (ASGs). Together, they provide a powerful way to control traffic flow and enforce security at scale.
What is a Network Security Group (NSG)?
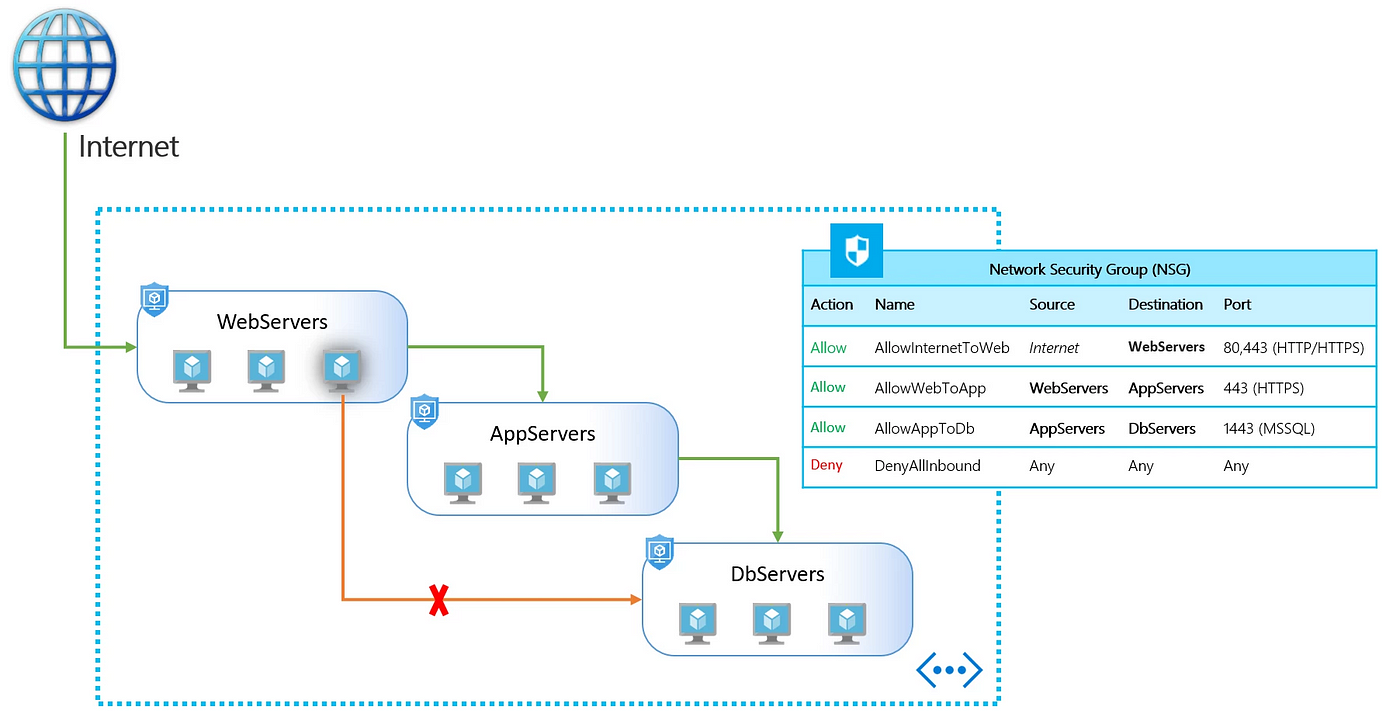
An NSG is like a virtual firewall for your Azure resources. It allows you to control inbound and outbound traffic to network interfaces (NICs), VMs, subnets, and more.
You define security rules based on:
Example Use:
Block all inbound traffic except SSH (port 22) and RDP (port 3389). Allow only web traffic (port 80/443) outbound.
What is an Application Security Group (ASG)?
An ASG is a logical group of VMs. It lets you group resources by application role—like "WebServers" or "DBServers"—rather than managing individual IPs.
You can then reference ASGs in NSG rules, making it easier to manage access in large environments.
Example Use:
Allow only VMs in the "WebServers" ASG to talk to the "DBServers" ASG over port 1433 (SQL). No need to update IPs manually as VMs are added or removed!
NSG + ASG: Better Together
While NSGs enforce the traffic rules, ASGs make those rules easier to manage. Together, they offer:

For secure, scalable, and manageable network security in Azure, mastering NSGs and ASGs is a must. Whether you're segmenting workloads or locking down environments, these tools give you the control you need—with less manual overhead.